 Cisco ASA stands for Cisco Adaptive Security Appliance.
Cisco ASA stands for Cisco Adaptive Security Appliance.
Cisco ASA acts as both firewall and VPN device.
This article explains how to setup and configure high availability (failover) between two Cisco ASA devices.
On a production environment, it is highly recommended to implement two Cisco ASA firewall (or VPN) in high available mode. This way, if the primary ASA fails, the secondary becomes active automatically without any downtime.
The following diagram explains on a high-level the ip-address that are assigned to the primary and secondary cisco ASA devices in this example.
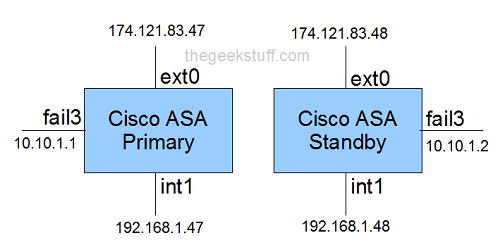
In the above diagram:
- ext0 – Assign your external ip-address to this interface. ext0 indicates that this is connected to the port 0 on the device.
- int1 – Assign your internal ip-address to this interface. int1 indicates that this is connected to the port 1 on the device.
- fail3 – Assign an internal ip-address to this interface that will be used between the primary and secondary devices during failover. fail3 indicates that this is connected to the port 3 on the device.
On the Cisco ASA 5520 model, it has 4 ports on the back, marked as 0, 1, 2 and 3. In our example, we’ll be using port 0, 1, and 3 as explained above.
Other than the 4 network ports, you’ll also see slots marked as mgmt, usb, usb, console, aux, flash card.
While the example mentioned here was done on Cisco ASA 5520 model, the same configurations will work on other Cisco ASA 5500 series. i.e Cisco ASA 5510, Cisco ASA 5505 etc.,
1. Setup failover interface on Primary ASA
Connect your laptop serial port to the primary ASA device using the console cable that came with the device.
Use PuTTY -> Select “Serial” -> Make sure serial line is set to “Com1” -> and speed is set to “9600”
Execute the following commands to mark the port 0/3 as failover lan unit primary.
enable config t failover lan unit primary interface gigabitEthernet 0/3 no shutdown
2. Assign the failover ip-address on Primary ASA using LANFAIL
Execute the following commands which will assign “10.10.1.1” (the one marked as fail0 in the diagram above) to the 0/3 interface on the primary device. This device should also know what is the failover ip-address of the standby. In this example, it is 10.10.1.2
You should also specify a failover key. Make sure the same key is used when you are configuring failover on the secondary device. In this example, the failover key is “secretkey”
failover lan interface LANFAIL gigabitethernet 0/3 failover interfaces ip LANFAIL 10.10.1.1 255.255.255.0 standby 10.10.1.2 failover key secretkey failover link LANFAIL exit show failover
3. Assign the External ip-address on Primary ASA
Execute the following commands which will assign “174.121.83.47” (the one marked as ext0 in the diagram above) to the 0/0 interface on the primary device. This device should also know what is the external ip-address of the standby ASA device. In this example, it is 174.121.83.48
show run config t interface gigabitEthernet 0/0 nameif external ip address 174.121.83.47 255.255.255.0 standby 174.121.83.48 no shutdown exit
4. Assign the Internal ip-address on Primary ASA
Execute the following commands which will assign “192.168.1.47” (the one marked as int0 in the diagram above) to the 0/1 interface on the primary device. This device should also know what is the internal ip-address of the standby ASA device. In this example, it is 192.168.1.48
interface gigabitEthernet 0/1 nameif internal security-level 100 ip address 192.168.1.47 255.255.255.0 standby 192.168.1.48 no shutdown exit show run
5. Verify the configuration on Primary ASA
Execute the following commands to verify the failover configuration that has been setup so far on the Cisco ASA primary device.
monitor external monitor internal exit show failover failover exit show failover interface show failover
6. Setup failover interface on Secondary ASA
Connect your laptop serial port to the secondary ASA device using the console cable that came with the device.
Use putty -> Select “Serial” -> Make sure serial line is set to “Com1” -> and speed is set to “9600”
Execute the following commands to mark the port 0/3 as failover lan unit secondary
en config t no failover failover lan unit secondary interface gigabitEthernet 0/3 no nameif no shutdown failover lan interface LANFAIL gigabitEthernet 0/3
7. Assign the failover ip-address on Secondary ASA using LANFAIL
Execute the following commands which specifies the primary LANFAIL ip-address is 10.10.1.1 and standby is 10.10.1.2
You should also specify a failover key. Make sure the same key that you used while configuring primary ASA is used here also. In this example, the failover key is “secretkey”
failover interface ip LANFAIL 10.10.1.1 255.255.255.0 standby 10.10.1.2 failover key secretkey failover link LANFAIL failover exit show run
8. Automatic Configuration Copy from Primary to Secondary ASA
On you configure the LANFAIL as shown above, all other configurations are automatically copied from the primary Cisco ASA device to the standby cisco ASA device.
show failover config t interface gigabitEthernet 0/3 no shutdown exit show failover
9. Setup Additional Configuration on ASA Primary
Setup additional configurations on the Cisco ASA primary device as shown below. This includes, hostname setup, domain name setup, route setup, allow http and ssh on internal ip-address for the cisco ASA primary.
config no monitor management hostname FW-PRIMARY domain name thegeekstuff.com router external 0.0.0.0 0.0.0.0 174.121.83.0 exit config t http 192.168.0.0 255.255.0.0 internal ssh 192.168.0.0 255.255.0.0 internal
Note: All the above configuration will be copied over automatically to the Cisco ASA standby device, as the failover is already configured. The only thing you need to setup on Cisco ASA standby is the hostname as “FW-STANDBY” as shown below.
config t hostname FW-STANDBY
Finally, view the current running configuration, and write it to the memory as shown below.
show run write mem






 My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
Comments on this entry are closed.
excellent as usual!thanks alot!
just a fantastic article. everything one needs to setup failover on an ASA. Many thanks good sir!
Really,Really, that was big help.
Thanx alot.
Excellent, I follow it and its running very well.
Your mask should be a 255.255.255.252 for just 2 IP addresses, not a full class C.
What about the link state interface? Don’t you need that as well?
nm I see failover link in there
Hi,
nice guide. One question. For example If i have 2 FW and 2 SW
FW1 – FW1
I I
I I
SW1 – SW2
gi 0/1 for example is inside interface of FW with ip 192.168.1.1 and stdb 192.168.1.2
to which ip i need to use 0.0.0.0.0 0.0.0.0
?
Just to inside FW interface?
0.0.0.0.0 0.0.0.0 192.168.1.1 (ip of primary unit) and in case of FW1 loss standby unit should automatically assign lan ip of primary unit? or we need to create another route with higher metric?
Regards
Anton
Great article. How do you inter-connect the two firewall? By a cross-over cable?
Nice and Clear article !!
Thks 🙂
Awesome very nice article, I have a question with this HA fail-over configuration, I also have dual link with two separate ISP, and I would like to setup for redundant backup ISP link. Could you please advise and provide the step to configure ASA.
Greatly appreciate your response
Its Best artical to clear basic concept of HA
Thank you Ramesh, Very helpful guide.
@ Anton.. 0.0.0.0.0 0.0.0.0 192.168.1.1 (ip of primary unit) and in case of FW1 loss standby unit should automatically assign lan ip of primary unit. No need to assign floating route.
In this case asa appliance act in router mode or in transparent mode ?
Good article simple but effective. direct to the point. 🙂
Hi Ramesh,
How about if either of the internal or external interfaces failed, does the failover switch to the FW where the interface are up?
Regards,
Melvin
Please confirm when we copy configurations so VPN pre shared key has been already copied with configurations and does it work once we upload same confifigurations through TFTP.
I have an ASA with several Subinterfaces. For Failover do I need to monitor each subinterface or just monitoring the main interface will do. ?
thanks
Hi, thank you for the article. The only part I don’t understand is why you are assigning a separate internal IP address for each device (and a separate external IP address for each device). Shouldn’t the inside interfaces SHARE an ip (i.e. through HSRP) as well as the external interfaces? You stated above “in case of FW1 loss standby unit should automatically assign lan ip of primary unit. No need to assign floating route” yet in your example you assigned a different IP address to the standby unit. Can you clarify? Thank you!
I have problem please and need to solve it. I need to connect the VPN tunnel between the site and primary ASA but I have no connect between them and I havnt reply from external ip of primary but I have replay frome the external ip of standby ASA. please can you help me?
I am in an environment where multiple ASA clusters have been set up and it appears that they have all been set to use the same host name. Can I change the host name on the standby member of the cluster w/o causing any undue harm? Most, if not all, of these clusters are using 8.0 to 8.3.
Tim, the article here is a bit misleading on the hostnames, you cannot give different hostnames for the active/standby. The failover setting will overwrite the hostname of the secondary to the primary’s if changed.
SL, the reason is purely management on the secondary when it is the standby. HSRP is not for ASA’s and not applied here, this is hardware redundancy for ASA using cisco “failover”, hsrp is for redundancy of routers by sharing a virtual ip.