VPN stands for Virtual Private Network.
A Virtual Private Network enables a computer to send and receive data from one private network to another private network which are connected via public network (Internet).
This is helpful for those who are outside the company’s intranet, and like to connect to office network securely to access the internal servers. VPN is also helpful when you are connecting multiple branch offices together.
Even when you are not connecting multiple branch offices together, you can still use VPN setup to allow your employees to connect remotely from their laptop to the datacenter and access the systems.
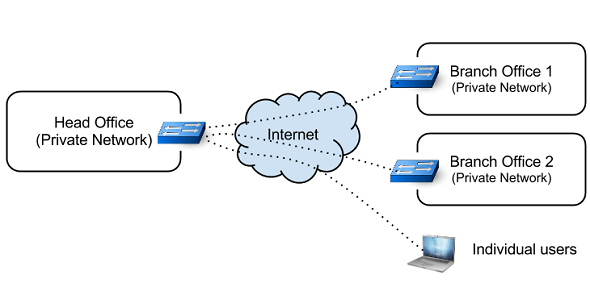
Sometimes company will buy leased lines to form WAN ( Wide Area Network ), and communicates with its branches. Though Leased line is secure and reliable, it is expensive.
VPN fills the gap by providing a point-to-point virtual connection via public network. A VPN can grow to accommodate more users across different geographical locations easily.
Types of VPN
On a high-level, the following are two types of VPN:
- Remote Access
- Site-To-Site
Remote Access is connecting a individual computer to a network via VPN. “Site to Site” is connecting two networks together via VPN.
What is OpenVPN
From OpenVPN man:
OpenVPN is an open source VPN daemon by James Yonan. OpenVPN is a robust and highly flexible VPN daemon. OpenVPN supports SSL/TLS security, ethernet bridging, TCP or UDP tunnel transport through proxies or NAT, support for dynamic IP addresses and DHCP, scalability to hundreds or thousands of users, and portability to most major OS platforms.
This tutorial explains process to setup and configure OpenVPN server and client for Remote Access.
I. Configuring OpenVPN – Server Side
1. Install OpenVPN
Install the openvpn package on both the server and the client machine.
$ sudo apt-get install openvpn
Use the respective package manager of the distribution that you are working. If you are using yum, do the following
$ yum install openvpn
2. Create Directories and set Env Variables
Create a directory inside /etc/openvpn and copy the easy-rsa contents to it. This is done to make sure that changes done to the scripts will not be lost when the package is upgraded. Change the owner as current user so that current user has permission to create files.
$ sudo mkdir /etc/openvpn/easy-rsa $ sudo cp /usr/share/doc/openvpn/examples/easy-rsa/2.0/* /etc/openvpn/easy-rsa $ sudo chown -R $USER /etc/openvpn/easy-rsa/
Next, Edit the /etc/openvpn/easy-rsa/vars to adjust to your environment.
export KEY_COUNTRY="IN" export KEY_PROVINCE="TN" export KEY_CITY="CHN" export KEY_ORG="tgs" export KEY_EMAIL="admin@thegeekstuff.com"
3. Creating the CA – Certificate Authority (Root Certificate)
The next step in building openvpn server is to establish a Public Key Infrastructure so that the server and clients can authenticate one another.
$ cd /etc/openvpn/easy-rsa/ $ source vars $ ./clean-all $ ln -s openssl-1.0.0.cnf openssl.cnf $ ./build-ca Generating a 1024 bit RSA private key ........++++++ ......++++++ unable to write 'random state' writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [IN]: State or Province Name (full name) [TN]: Locality Name (eg, city) [CHN]: Organization Name (eg, company) [tgs]: Organizational Unit Name (eg, section) [changeme]: Common Name (eg, your name or your server's hostname) [changeme]: Name [changeme]:lakshmanan Email Address [mail@host.domain]:admin@thegeekstuff.com
Once ./build-ca is completed, you will see a file named “ca.key” and “ca.crt” inside /etc/openvpn/easy-rsa/keys/
Remember that the “.key” files has to be kept confidential.
4. Creating certificate for Server
The next step is to create a certificate for our Openvpn server.
$ /etc/openvpn/easy-rsa/build-key-server vpnserver ... ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y
Note that vpnserver is the HOSTNAME of the server. This command will take input from the user similar to the previous one. This command will create the certificate and key files for the server.
5. Creating certificate for client
The VPN client will also need certificate to authenticate with server. If you want to configure multiple clients, you need to create certificate for each client separately.
$ ./build-key vpnclient1 ... ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y
vpnclient1 is the hostname of the client. This command will create the certificate and key files for the client.
6. Create Diffie Hellman parameters
$ ./build-dh
Once all the above steps are successfully completed, you will have many key and certificate files inside /etc/openvpn/easy-rsa/keys.
7. Copy the certificates to respective locations
We have created Root Certificate, Server Certificate and Client Certificate. We need to copy those to appropriate locations.
$ cd /etc/openvpn/easy-rsa/keys/ $ sudo cp ca.crt vpnserver.crt vpnserver.key dh1024.pem /etc/openvpn/ $ scp ca.crt vpnclient1.key vpnclient1.crt root@vpnclient1:/etc/openvpn
Now we have copied the client certificate and key to the client machine. Remember to use a secure medium like scp, while copying the key files.
8. Configuring the Server
OpenVPN provide a default server.conf. You can modify it to suit the needs.
$ sudo cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz /etc/openvpn/ $ sudo gzip -d /etc/openvpn/server.conf.gz
Edit the “/etc/openvpn/server.conf“.
... ca ca.crt cert vpnserver.crt key vpnserver.key dh dh1024.pem ...
Now start the OpenVPN server:
$ sudo /etc/init.d/openvpn start
* Starting virtual private network daemon(s)...
* Autostarting VPN 'server'
$ ifconfig tun0
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.1 P-t-P:10.8.0.2 Mask:255.255.255.255
By default openVPN will log errors in syslog file.
II. Configuring OpenVPN – Client Side
9. Setup Client Config Files
Now we will configure the openVPN to work as client. Remember that we have already installed the openvpn package in client, and we have “ca.crt”, “vpnclient1.key”, vpnclient1.crt” in /etc/openvpn/
Copy the sample client.conf to /etc/openvpn.
$ sudo cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf /etc/openvpn/
Edit the /etc/openvpn/client.conf.
... # Specify that this is openvpn client client remote vpnserver 1194 ca ca.crt cert vpnclient1.crt key vpnclient1.key ...
Now start the OpenVPN in client
$ /etc/init.d/openvpn start
* Starting virtual private network daemon(s)...
* Autostarting VPN 'client'
$ ifconfig tun0
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.6 P-t-P:10.8.0.5 Mask:255.255.255.255
10. Test the VPN Setup
Ping the vpnserver from the client machine to see whether VPN is working or not.
$ ping 10.8.0.1 PING 10.8.0.1 (10.8.0.1) 56(84) bytes of data. 64 bytes from 10.8.0.1: icmp_req=1 ttl=64 time=2.14 ms
If you are able to ping, then you have made the right setup.
Please keep the following in mind:
- Make sure that the client and server use same protocol and port number.
- Client and server must use same config regarding some parameters like keysize, compression etc…
- In case of any problem, increase the log verbosity in the configuration and check the syslog file for troubleshooting.






 My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
Comments on this entry are closed.
Hi,
Very nice and useful article..
Thanks
Thanks Nice tutorial
Hi,
Very informative article as usuall,
Do you know of any tools to administer and audit Openvpn.
Thanks,
Thank you for this howto ^_^. But one thing that was miss out is to use the epel repo before you can install via yum cause openvpn its not part of the usual repository. I used CentOS.
Very nice article I must say. One suggestion would be is to include info about the “ta.key”. You can find helpful reference about it in Arch’s wiki.
Hi,
Thanks alot for the usefull and nice article.I also have a query related to openvon
1) is it possible to configure the OVPN server to lease the DHCP ip to ovpn client for specific time say 2 hours or so
2) The speed of the interface that is created in the server can be increased? as I can see my Speed in the server to be 10M
Settings for as0t0:
Supported ports: [ ]
Supported link modes:
Supports auto-negotiation: No
Advertised link modes: Not reported
Advertised auto-negotiation: No
Speed: 10Mb/s
Duplex: Full
Port: Twisted Pair
PHYAD: 0
Transceiver: internal
Auto-negotiation: off
Current message level: 0xffffffa1 (-95)
Link detected: yes
Could it be possible with this method to create a server in order to play a particular game with other people?
Doing right now!
Thanks for your time in doing this tutorial
As usual, Excellent article.
Nice Article. I’ve been thinking of using openvpn to secure a radio link between 2 buildings where the only security the radios offer is wep. Thanks!
Thank you.
This certainly makes it simple to setup. Only thing that was not covered is how it works. For example, how does the server 10.1.2.3 know how to find a client on 192.168.1.3 if its going through a double NAT to get there. Also, what about going through firewalls? Is anything needed there such as opened ports. I would appreciate understanding how VPN addresses these issues.
Thanks, very informative.
Will try to use it to setup a test on my VPS>
Hello Sir,
I have configured Openvpn server. and its working perfect. then i have try to configure site-to-site openvpn. but its not connect to eachother. confused how to route both server. so kindly help me or article for Site-to-Site.
What are the things to take care in server configuration file?????
:
IMPORTANT
I can’t download VPN in my coolpad 5310?
I am work on OPENVPN Setup in fedora 23, I have setup and connect server and client using OPENVPN, After I vpn connect, I need to access server system.
See My Final Status here
Then Add my Openvpn GUI setup then connect vpn here
I connected both server and client system , But I dont know how to access sever system via client. our server addr ping in client and client addr also ping with server side, then how to access server system via client and access server file after ending your tutorial steps.
if try to access server file via nautilus,
syntax : smb://chexxxxx@192.xx.xx.xxx
but throw error
Unhandled error message: Failed to retrieve share list from server: No route to host
Suggest me how to access server system after finish your tutorials steps and accees server file from client.
change dh1024 to dh2048 !